Container Security Services
Securing your business from vulnerabilities through container applications
What is Docker Container Security?
With the growing implementation of container technologies in commercial systems, containers have become prime targets for malicious actors. A single compromised container can serve as an entry point into an organization’s broader environment.
Container security is essential for protecting containerized applications from potential attacks by integrating security tools and policies. It addresses threats across the entire environment, including the software supply chain, CI/CD pipeline, infrastructure, container runtime, and lifecycle management applications.
Benefits of Container Security Services
Container security is not just about protecting a containerized application and its infrastructure against cyber threats; it also enhances your organization’s overall IT security. It secures your container management stack across cloud, hybrid, and on-premises environments, facilitating the generation, distribution, and deployment of container images while uncovering security issues throughout the container lifecycle.
Key benefits include:
- Enhanced security for build pipeline images and runtime environments
- Protection across all layers: container images, hosts, platforms, and applications
- Improved compliance and risk management
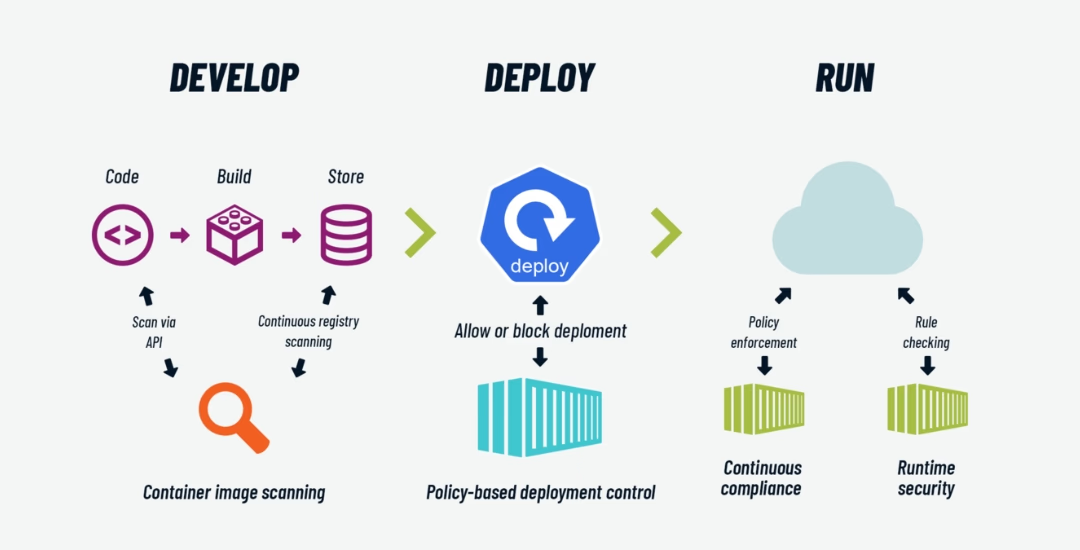
Key Components of Container Security

Image Security Assessment
Conduct vulnerability scans on container images to identify outdated packages, vulnerabilities, and misconfigurations. This process also involves removing unnecessary components and services while securing user access and communication channels.

Orchestration Platform Security
Implement role-based access controls, restrict unnecessary permissions, and enforce network policies in line with security guidelines. Establish robust secret management systems to handle credentials and keys securely.
Runtime Security Monitoring
Employ techniques to detect, alert, and respond to suspicious activities effectively, ensuring ongoing security during runtime.

CI/CD Pipeline Security
Integrate security testing into the CI/CD pipeline to identify and address vulnerabilities early in the development lifecycle. Ensure that container images are signed and verified for authenticity to mitigate the risk of tampering or deploying malicious images.
By investing in container security services, you can significantly strengthen your security posture, safeguard critical applications, and enhance compliance throughout the container lifecycle.
Hackers Never Sleep. Neither Do We.
DUBAI OFFICE
+971-54-565-9528
Digisecuritas Cybersecurity, FZCO 52550-001, IFZA Business Park, Dubai Digital Park, Dubai Silicon Oasis, Dubai, UAE
INDIA OFFICE
+91-8196966161, +91-8194943131
SCO 27, Level-II, Sector 21C, Sector 21, Chandigarh, 160022
