Incident Response Plan Creation
The incident response process is critical for organizations to effectively manage and mitigate cybersecurity incidents. Two widely recognized frameworks for incident response are developed by NIST and SANS, each outlining essential steps for effective management.
An effective incident response plan (IRP) is essential for organizations to manage and mitigate cybersecurity incidents efficiently. Here are the critical components that should be included in a robust IRP:
- 1
-
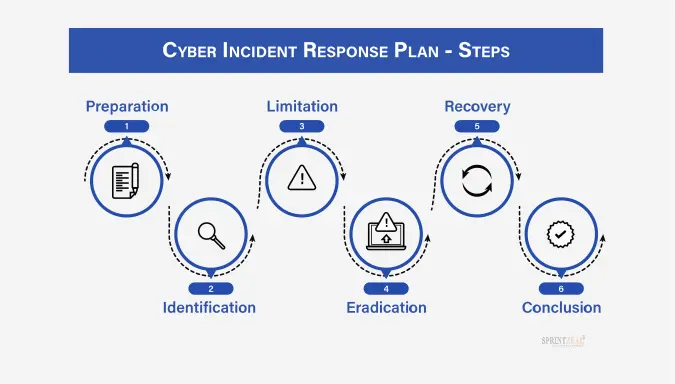
Preparation
- Establish a dedicated incident response team with clearly defined roles and responsibilities.
- Conduct regular training and simulations to prepare the team for potential incidents.
- Develop policies and procedures, ensuring that tools for detection and response are in place.
- 2
-
Incident Identification and Classification
- Implement processes for quickly identifying and categorizing incidents based on their severity and potential impact.
- Utilize monitoring tools to detect unusual activities that may indicate a security breach.
- 3
-
Communication Plan
- Create a clear communication strategy outlining how information about incidents will be shared internally and externally.
- Include templates for consistent messaging to stakeholders during an incident.
- 4
-
Containment, Eradication, and Recovery
- Develop strategies for containing the incident to prevent further damage.
- Outline steps for eradicating the threat from systems and restoring affected services to normal operation.
- Specify recovery procedures to ensure business continuity.
- 5
-
Post-Incident Analysis
- Conduct a thorough review of the incident after it has been resolved to identify lessons learned.
- Analyze what worked well and what didn’t, updating the IRP based on these insights to improve future responses.


- 6
-
Continuous Improvement
- Regularly review and update the incident response plan to adapt to new threats and changes in the organizational environment.
- Incorporate feedback from post-incident analyses into training programs and policy revisions.
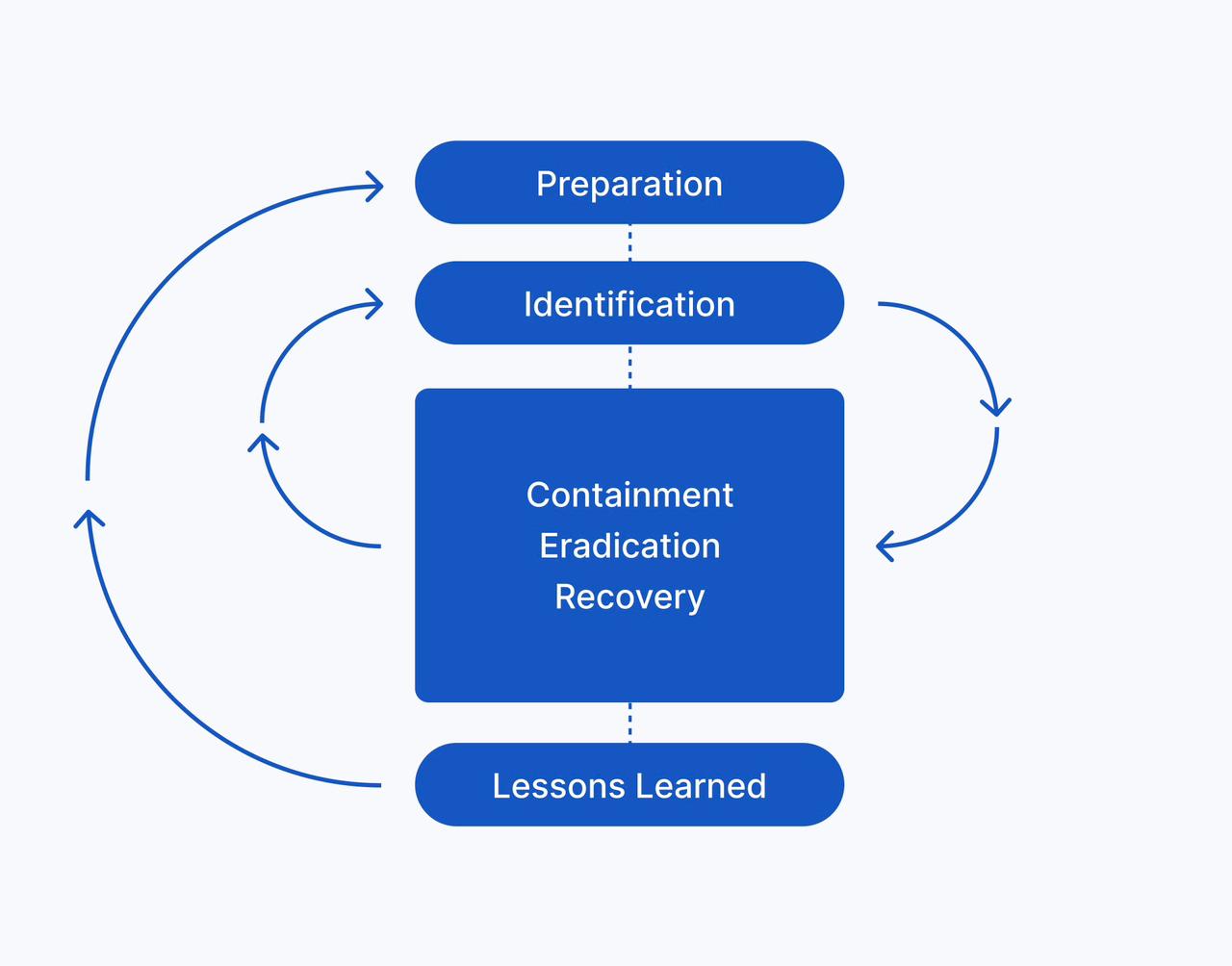
NIST Incident Response Steps
- Preparation: Establish a Computer Security Incident Response Team (CSIRT) with defined roles and responsibilities. Ensure that plans are regularly updated and that the team has the necessary tools and training.
- Detection and Analysis: Identify signs of an incident, assess its severity, and document all findings. Prioritize incidents based on their potential impact on business operations.
- Containment, Eradication, and Recovery: Implement strategies to contain the incident, eliminate its root cause, and restore normal operations while preserving evidence for future analysis.
- Post-Incident Activity: Conduct a thorough review of the incident to identify lessons learned. This step is crucial for improving future responses and enhancing overall security measures.


SANS Incident Response Steps
- Preparation: Similar to NIST, this step involves readiness through planning and training.
- Identification: Focus on recognizing incidents as they occur.
- Containment: Take immediate action to limit the impact of the incident.
- Eradication: Remove the cause of the incident from the environment.
- Recovery: Restore systems to normal operations while ensuring that vulnerabilities are addressed.
- Lessons Learned: Analyze the incident to improve future responses and update policies accordingly.
Comparison of Frameworks
While both frameworks share similar components, they differ slightly in terminology and structure. The NIST framework emphasizes overlapping containment, eradication, and recovery processes, while SANS separates these into distinct steps.

Conclusion
By incorporating these components, organizations can create a comprehensive incident response plan that not only addresses immediate threats but also fosters a culture of continuous improvement in cybersecurity practices. This proactive approach ensures that organizations are better equipped to handle incidents effectively while minimizing damage and maintaining trust with stakeholders.
Hackers Never Sleep. Neither Do We.
DUBAI OFFICE
+971-54-565-9528
Digisecuritas Cybersecurity, FZCO 52550-001, IFZA Business Park, Dubai Digital Park, Dubai Silicon Oasis, Dubai, UAE
INDIA OFFICE
+91-8196966161, +91-8194943131
SCO 27, Level-II, Sector 21C, Sector 21, Chandigarh, 160022
