Vulnerability Management
Definition & Process
Vulnerability management is crucial for endpoint security and serves as a proactive measure to identify and eliminate security weaknesses before they lead to breaches. This article outlines the essentials of vulnerability management and explores the step-by-step process using tools like Vulnerability Manager Plus
What is Vulnerability Management?
Vulnerability management is a structured process designed to identify, assess, and fix security vulnerabilities in an organization’s systems. It includes scanning for weaknesses, prioritizing risks, and applying remediations to minimize exposure to cyber threats. This ongoing process strengthens an organization’s ability to fend off attacks and reduce vulnerabilities.
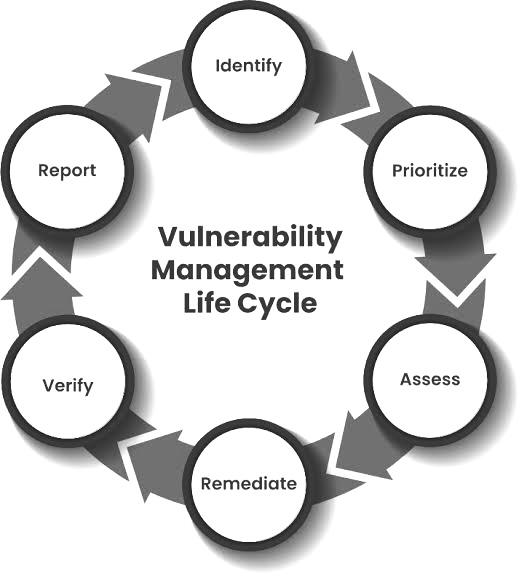
Why Do You Need Vulnerability Management?
A 2020 Forrester Global Security Survey revealed that 49% of organizations experienced one or more breaches within a year, with software vulnerabilities playing a significant role. Moreover, in 2019, 22,316 new security flaws were discovered, and over a third of them had known exploits. This highlights the necessity of incorporating vulnerability management into a cybersecurity strategy.
Since a single vulnerability can lead to data breaches, managing and prioritizing vulnerabilities is one of the top 10 security controls recommended by the Center for Internet Security (CIS).
Challenges in Vulnerability Management
Tracking the sheer volume of vulnerabilities is a major challenge, especially across thousands of diverse assets. With limited time and resources, many vulnerabilities go unaddressed, leaving organizations at risk. Other issues include:
- Lack of the right tools to prioritize vulnerabilities.
- Fragmented workflows, especially when patching requires third-party integrations.
- Vulnerabilities in misconfigurations that could be exploited for lateral movement by attackers.
- The need for a contingency plan for unpatchable vulnerabilities like end-of-life software or zero-day threats.
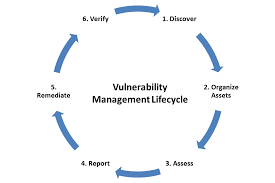

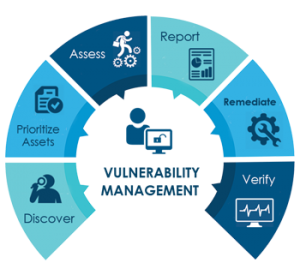
Vulnerability Management Process
Vulnerability management typically follows these steps:
- Asset Discovery – Identify and catalog all assets within your network.
- Vulnerability Scanning – Conduct scans to detect potential vulnerabilities.
- Assessment – Assess vulnerabilities based on risk factors, such as severity and exploit availability.
- Prioritization – Prioritize vulnerabilities by their potential impact and urgency.
- Remediation Planning – Develop a remediation strategy, often through patching or reconfiguring systems.
- Execution – Apply the necessary patches or mitigations.
- Verification – Verify that the remediation is effective.
- Reporting – Generate reports to track the status of vulnerabilities and remediation efforts.
Key Features of Vulnerability Management Tools
Tools like Vulnerability Manager Plus offer comprehensive security features to secure endpoints, such as:
- Automated Patching Deploy patches automatically to address known vulnerabilities.
- Security Configuration Management Monitor and enforce security configurations.
- High-risk Software Auditing Detect and audit software that may introduce risks.
- Web Server Hardening Strengthen the security of web servers hosting critical data.


Prioritization for Effective Patching
Vulnerability Manager Plus provides several capabilities to ensure critical vulnerabilities are addressed:
- Identifying vulnerabilities with severity scores.
- Knowing whether exploit code is publicly available.
- Monitoring how long a vulnerability has been in the network.
- Filtering vulnerabilities by their impact and available patches.
- Recommendations for handling high-priority vulnerabilities.
- Special attention to critical assets, including databases and web servers.
By adopting a structured approach to vulnerability management, organizations can mitigate risks, stay compliant, and safeguard their networks from evolving cyber threats.
Hackers Never Sleep. Neither Do We.
DUBAI OFFICE
+971-54-565-9528
Digisecuritas Cybersecurity, FZCO 52550-001, IFZA Business Park, Dubai Digital Park, Dubai Silicon Oasis, Dubai, UAE
INDIA OFFICE
+91-8196966161, +91-8194943131
SCO 27, Level-II, Sector 21C, Sector 21, Chandigarh, 160022
