Zero Trust Architecture Consulting
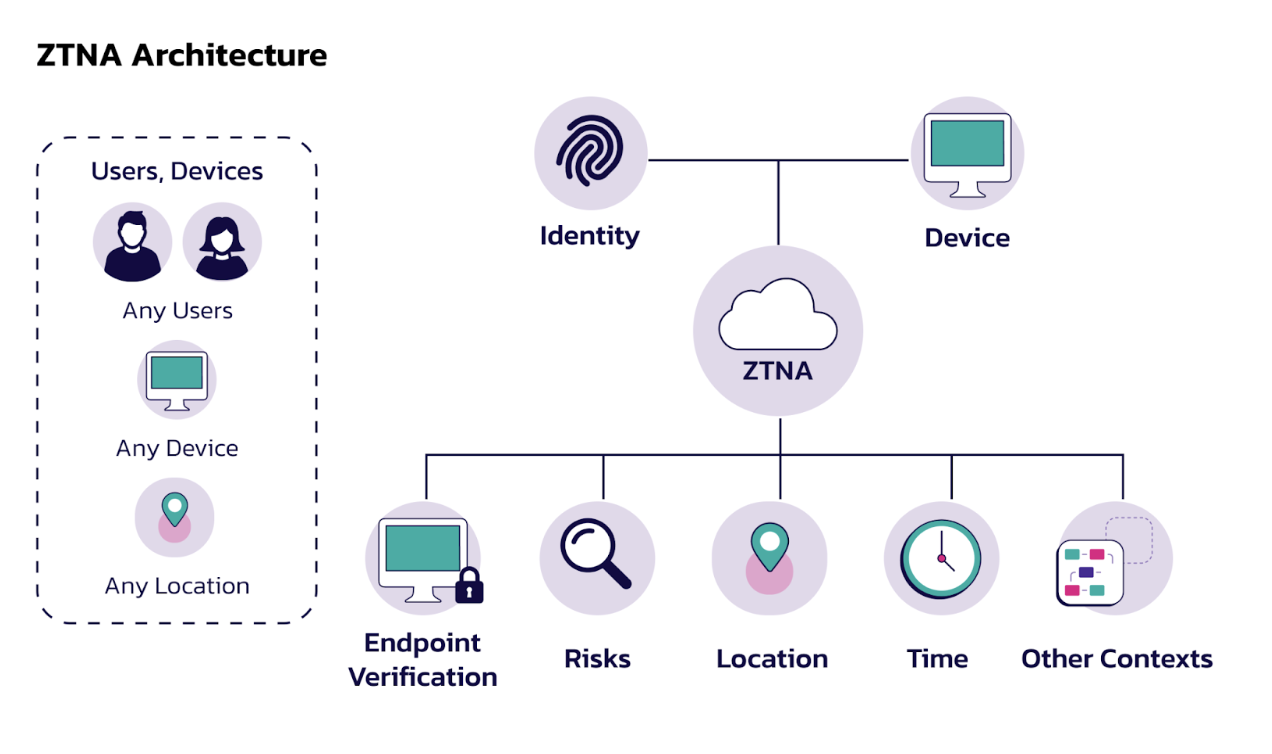
Zero Trust Architecture (ZTA) is a cybersecurity model that operates on the principle of "never trust, always verify." It emphasizes strict identity verification for every person and device attempting to access resources on a network, regardless of whether they are inside or outside the organizational perimeter. CyberSecOp offers a comprehensive suite of Zero Trust solutions and consulting services designed to enhance an organization's security posture.
- 1
-
Zero Trust Readiness Assessment
- A foundational evaluation that assesses an organization's current security posture and readiness to implement Zero Trust principles.
- This assessment provides insights into existing vulnerabilities and helps develop a tailored roadmap for Zero Trust adoption.
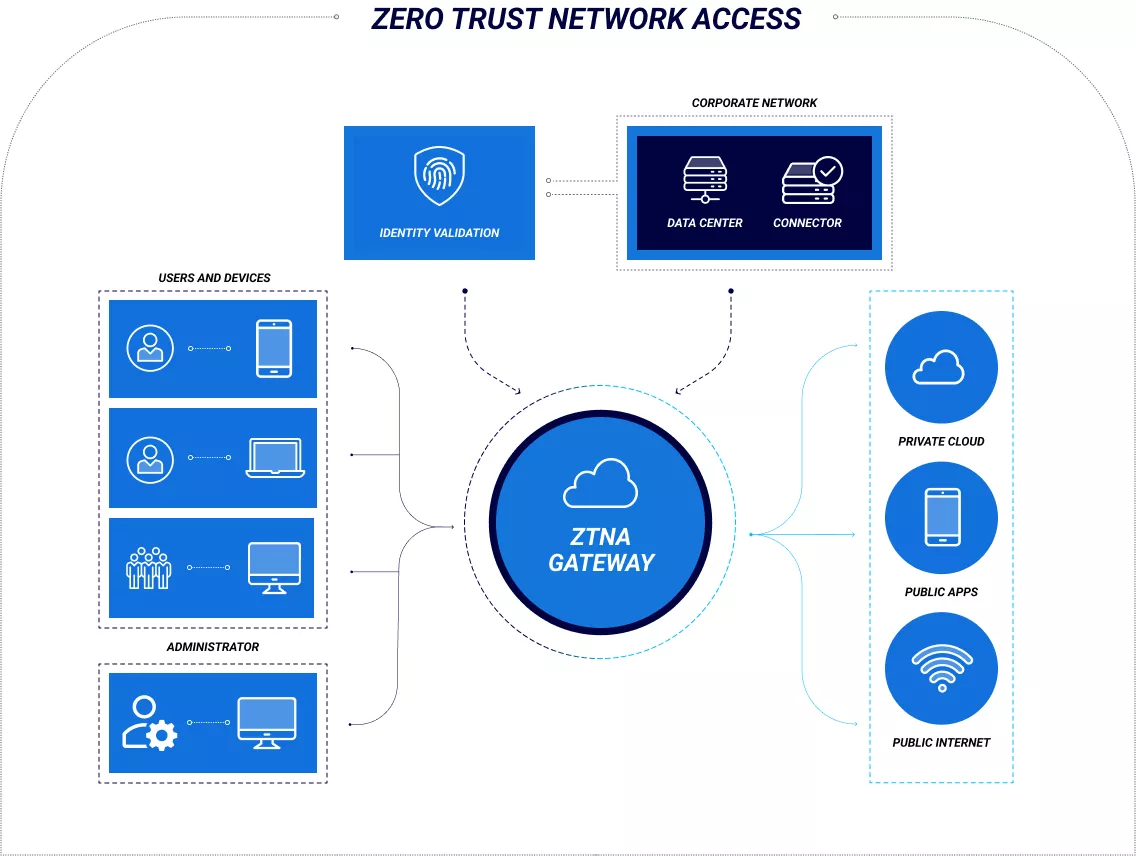
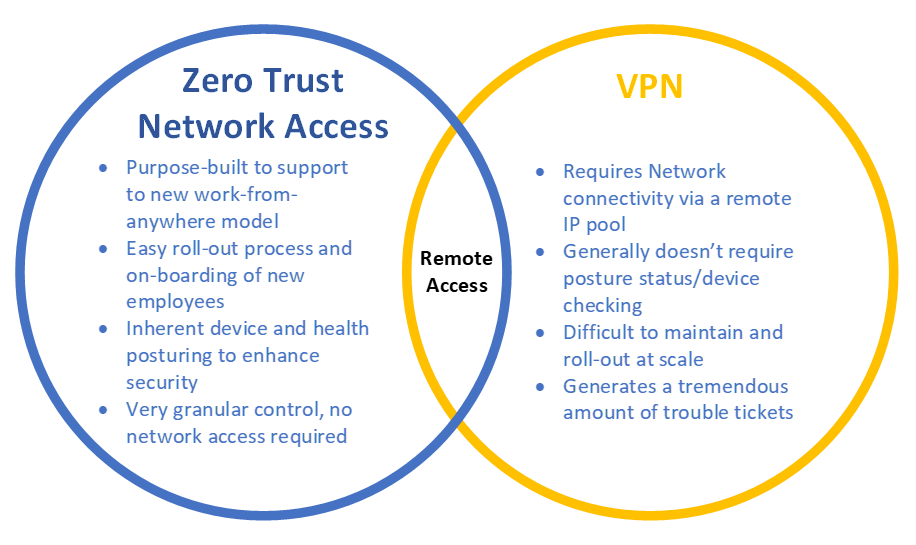
- 2
-
Implementation of Security Framework
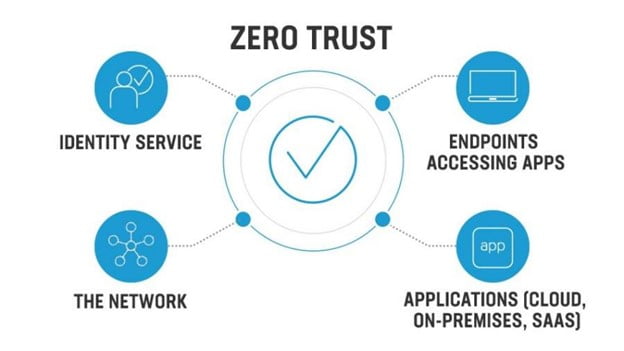
- CyberSecOp focuses on transforming businesses into a Zero Trust model by protecting five critical pillars: identity, devices, applications, data, and infrastructure.
- The approach includes establishing user-based access rules and segmenting access to sensitive data.
- 3
-
Continuous Monitoring
- Ongoing surveillance of network activity to detect and respond to malicious actions in real-time.
- This proactive monitoring is essential for maintaining a robust security posture.
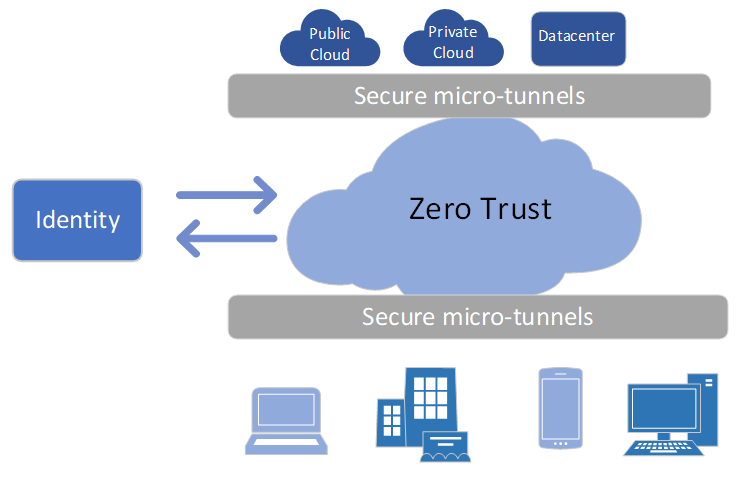
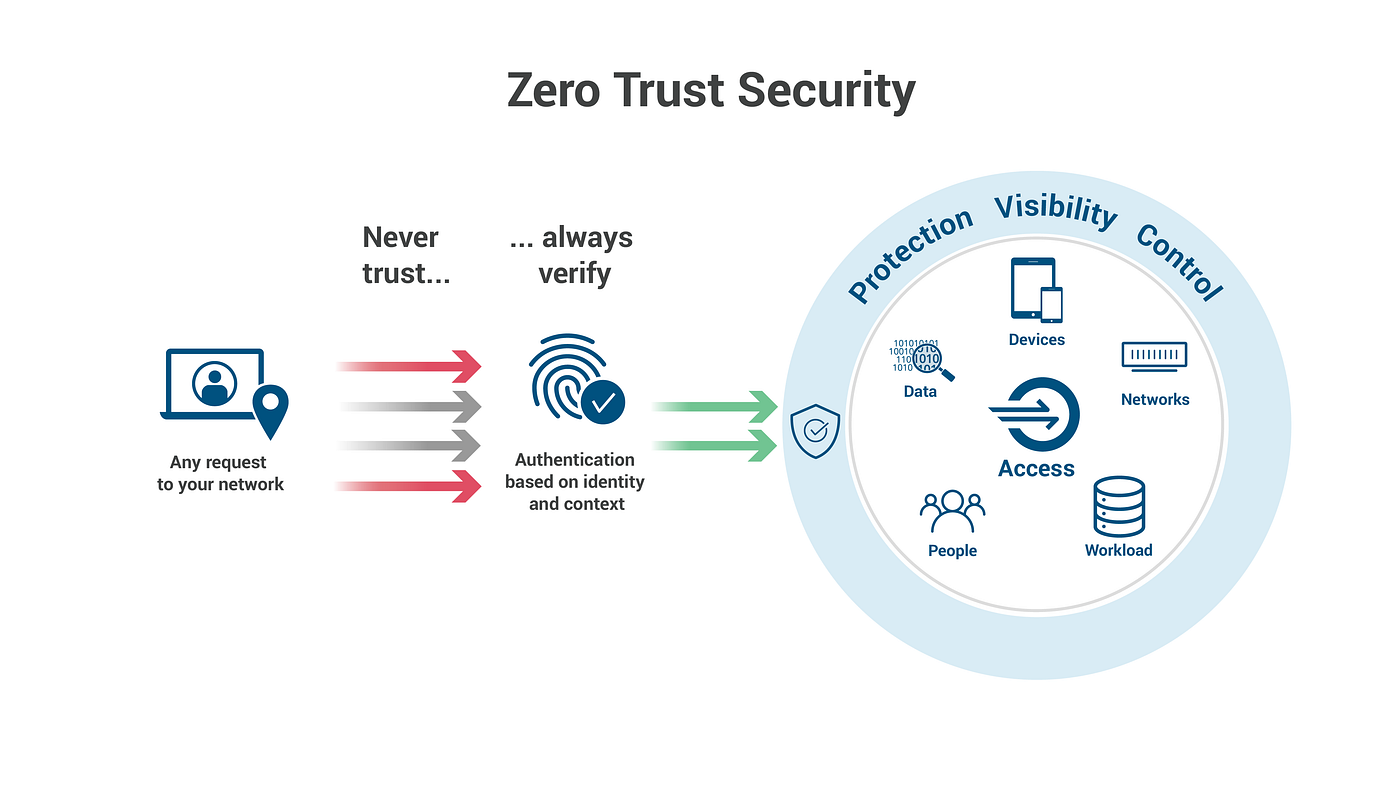
- 4
-
Multi-Layered Security Solutions
CyberSecOp employs various tools and technologies, including:
- Advanced Endpoint Protection: Safeguarding devices from malware without relying solely on traditional signature-based methods.
- Secure Web Gateway: Protecting against web-based threats while ensuring compliance with organizational policies.
- Data Loss Prevention (DLP): Monitoring and controlling sensitive data movement across networks.
- 5
-
Identity and Access Management
- Implementation of Single Sign-On (SSO) and Multi-Factor Authentication (MFA) to enhance user authentication processes.
- These measures ensure that only authorized users gain access to critical systems.
- 6
-
Incident Response and Threat Intelligence
- Providing actionable intelligence through Security Incident Event Management (SIEM) systems that analyze logs and events for potential threats.
- Establishing a robust incident response strategy to address security breaches effectively.
Benefits of Adopting Zero Trust Architecture
- Enhanced Security Posture: By verifying every access request, organizations can significantly reduce the risk of unauthorized access and data breaches.
- Improved Compliance: Implementing Zero Trust principles helps organizations meet regulatory requirements related to data protection and privacy.
- Scalability: The cloud-native nature of many Zero Trust solutions allows organizations to scale their security measures as their needs evolve.

Conclusion
CyberSecOp's Zero Trust Architecture solutions provide organizations with a comprehensive framework for securing their digital environments. By focusing on continuous monitoring, identity verification, and proactive threat management, businesses can enhance their cybersecurity resilience against evolving threats. Adopting a Zero Trust model not only protects sensitive data but also aligns security practices with organizational goals.
Hackers Never Sleep. Neither Do We.
DUBAI OFFICE
+971-54-565-9528
Digisecuritas Cybersecurity, FZCO 52550-001, IFZA Business Park, Dubai Digital Park, Dubai Silicon Oasis, Dubai, UAE
INDIA OFFICE
+91-8196966161, +91-8194943131
SCO 27, Level-II, Sector 21C, Sector 21, Chandigarh, 160022
