Security Policy and Framework Development
The development of an Information Security Policies Framework is crucial for organizations aiming to protect their information assets. This framework provides a structured approach to creating, implementing, and maintaining security policies that align with business objectives and regulatory requirements.
Key Components of the Framework
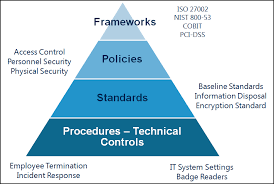
- Policy Development: Establishing clear and comprehensive security policies that define the organization’s stance on various security issues, including data protection, access control, and incident response.
- Risk Assessment: Conducting thorough risk assessments to identify vulnerabilities and threats to information assets. This process informs policy creation by highlighting areas that require specific attention.
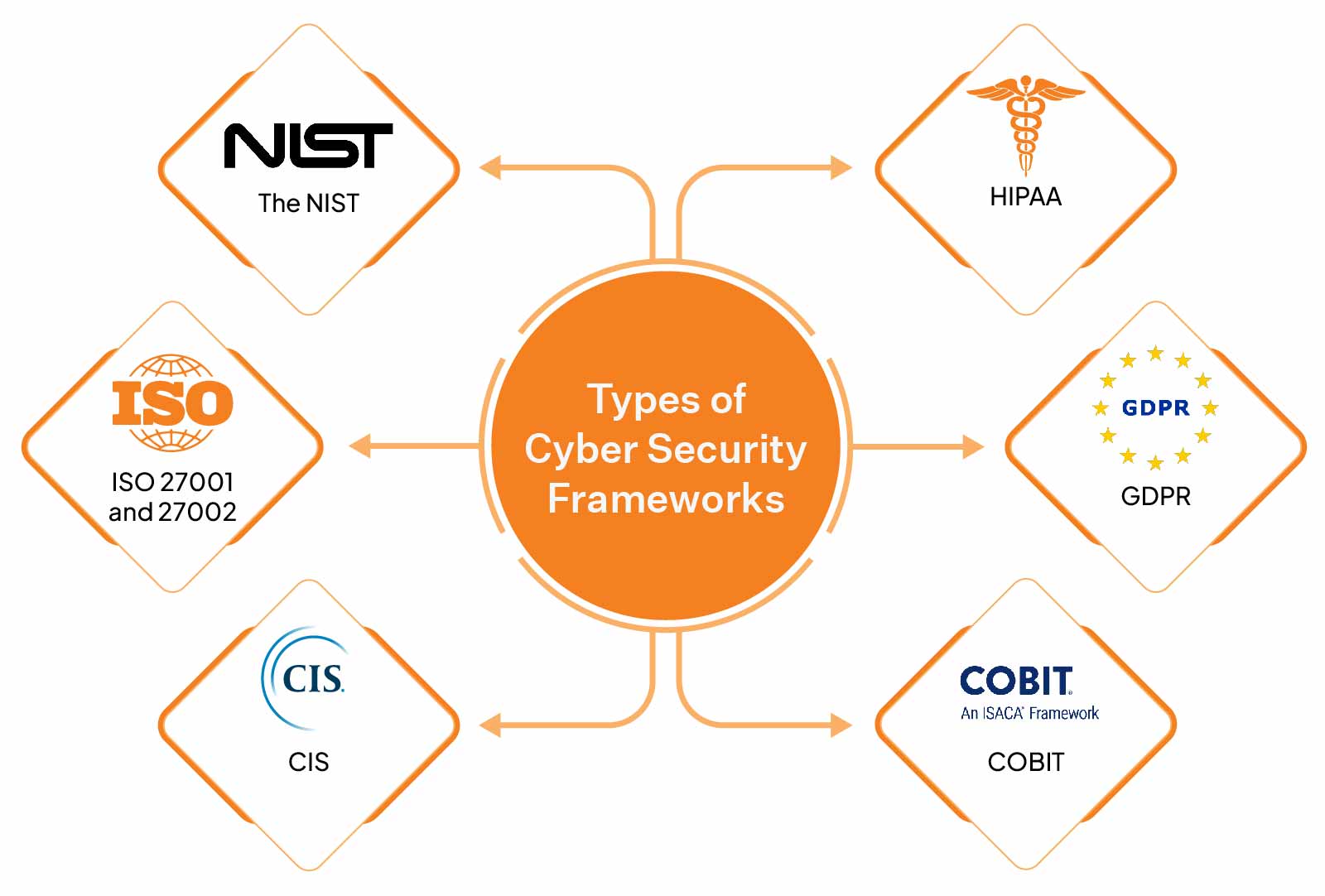
- Compliance Alignment: Ensuring that the policies comply with relevant laws, regulations, and industry standards. This alignment helps organizations avoid legal penalties and enhances their reputation.
- Training and Awareness: Implementing training programs to ensure that all employees understand the policies and their roles in maintaining information security.
- Continuous Improvement: Establishing mechanisms for regular reviews and updates of the policies to adapt to evolving threats and changes in the business environment.
Benefits of a Robust Information Security Policies Framework
- Enhanced Security Posture: A well-defined framework strengthens the overall security measures within the organization.
- Clear Responsibilities: Clearly articulated policies delineate roles and responsibilities, fostering accountability among employees.
- Risk Mitigation: By identifying and addressing potential risks proactively, organizations can reduce the likelihood of security incidents.
- Improved Compliance: A structured approach helps maintain compliance with applicable regulations, reducing the risk of fines or sanctions.
Conclusion
The Information Security Policies Framework is an essential tool for organizations looking to safeguard their information assets effectively. By focusing on policy development, risk assessment, compliance alignment, training, and continuous improvement, organizations can create a robust security environment that supports their business objectives while protecting against cyber threats.
Hackers Never Sleep. Neither Do We.
DUBAI OFFICE
+971-54-565-9528
Digisecuritas Cybersecurity, FZCO 52550-001, IFZA Business Park, Dubai Digital Park, Dubai Silicon Oasis, Dubai, UAE
INDIA OFFICE
+91-8196966161, +91-8194943131
SCO 27, Level-II, Sector 21C, Sector 21, Chandigarh, 160022
