Data Classification and Protection Strategy
Data classification and protection services are essential for safeguarding an organization's sensitive information. These services ensure that data is accurately classified, labeled, and secured according to its sensitivity level.
Key Components of Data Classification and Protection
- Identification and Classification:
- The initial step involves identifying sensitive data types, such as personally identifiable information (PII), financial records, intellectual property, and trade secrets.
- Once identified, this data is classified to determine the appropriate security measures needed.
- Access Controls and Encryption:
- Implementing robust access controls ensures that only authorized personnel can access sensitive data.
- Encryption is utilized to protect data both at rest and in transit, adding an additional layer of security.
- Data Protection Policies and Procedures:
- Developing comprehensive policies and procedures is crucial for guiding how sensitive data should be handled, transmitted, and stored securely.
- These policies help establish consistent practices across the organization.
- Employee Training:
- Training staff on data handling best practices is vital to ensure everyone understands their roles in protecting sensitive information.
- Regular training sessions help reinforce the importance of data security and compliance.
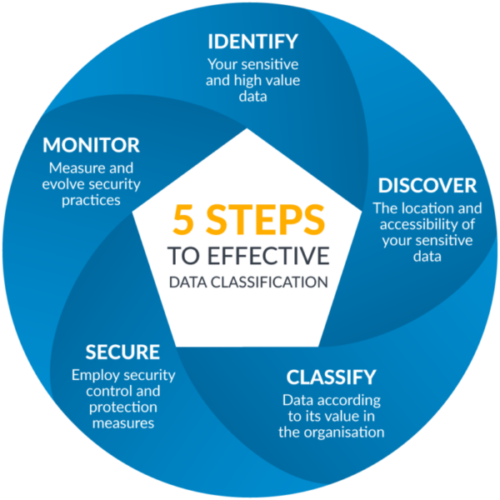
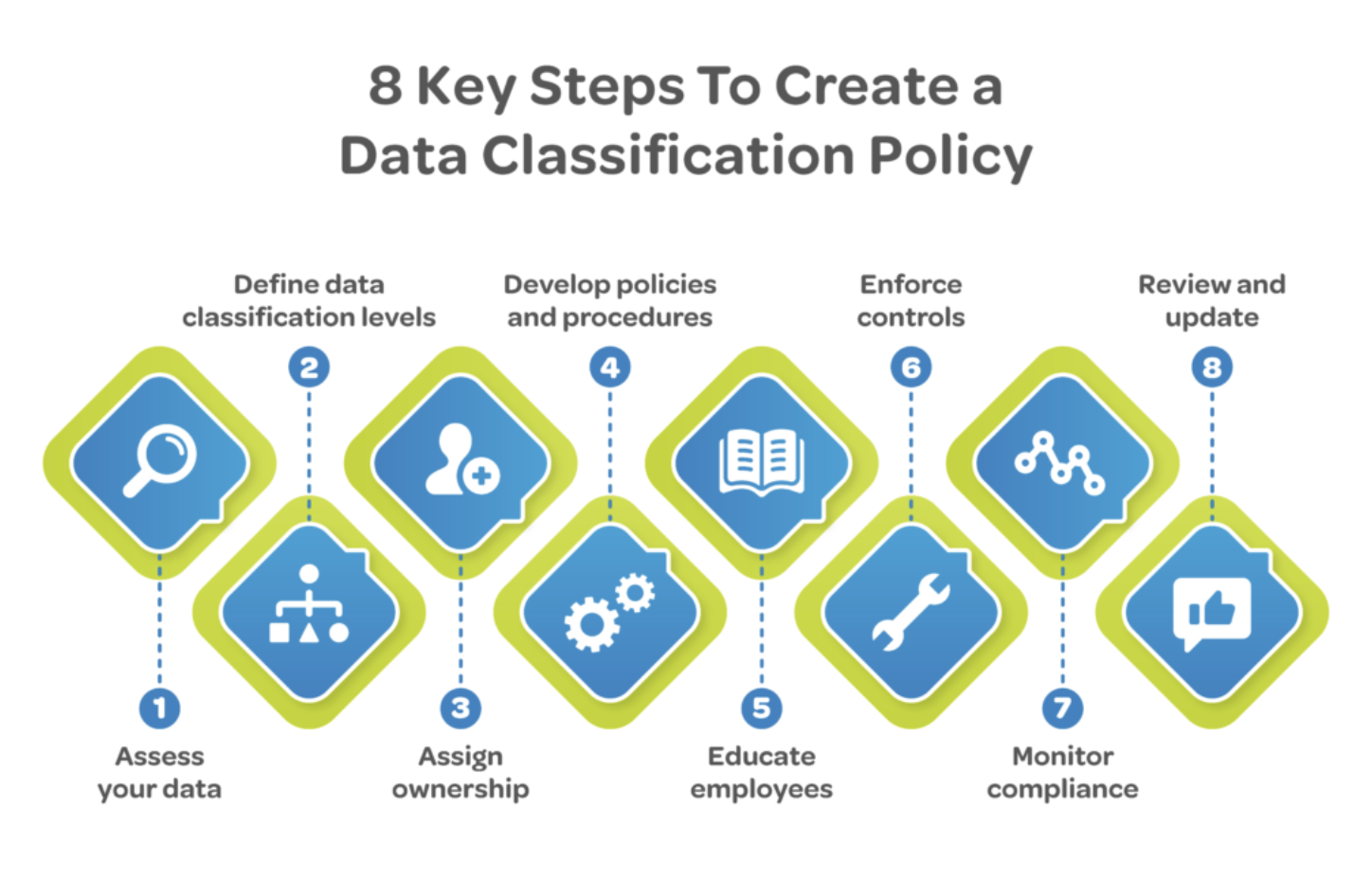
Objectives of Data Classification and Protection Services
The primary goal of these services is to protect sensitive data from unauthorized access, use, disclosure, modification, or destruction. This includes:
- Ensuring correct classification and labeling of sensitive information.
- Implementing appropriate controls throughout the data lifecycle.
- Assisting organizations in meeting regulatory compliance requirements.
- Preventing data breaches that could lead to reputational damage, financial loss, or legal liabilities.
Tailored Approach
Digisecuritas adopts a customized approach to data classification and protection based on each client's specific needs. The process begins with an assessment of the organization's data protection requirements, followed by the development of a comprehensive strategy that includes recommendations for classification, access controls, encryption, and policy implementation.By focusing on these critical aspects, organizations can enhance their data security posture and mitigate risks associated with sensitive information management.
Hackers Never Sleep. Neither Do We.
DUBAI OFFICE
+971-54-565-9528
Digisecuritas Cybersecurity, FZCO 52550-001, IFZA Business Park, Dubai Digital Park, Dubai Silicon Oasis, Dubai, UAE
INDIA OFFICE
+91-8196966161, +91-8194943131
SCO 27, Level-II, Sector 21C, Sector 21, Chandigarh, 160022
