Endpoint Security Management
With the rise of remote work and the increased use of off-premise and mobile devices for business purposes, corporate IT assets are more accessible than ever by devices that may not be owned or managed by the organization. Endpoint security management ensures that any device attempting to connect to corporate resources is compliant with security policies before access is granted.
Purpose of Endpoint Security Management
Endpoint security management systems are designed to limit the risks posed by endpoints like laptops and mobile devices, which may be non-compliant with security policies or infected with malware. These systems enforce security policies at scale, allowing administrators to define rules for specific device groups or types. This ensures consistent policy enforcement, regardless of the number or diversity of corporate endpoints.
Importance of Endpoint Security Management
As employees increasingly use personal or unsecured devices, the risk to corporate endpoints and data grows. These devices may lack compliance with security policies or be exposed to malware via unsecured networks or general internet use. The complexity of managing endpoint security rises alongside the expansion of corporate networks, making individual enforcement of security policies impractical.
Endpoint security management solutions are critical because they guard against threats that could bypass traditional perimeter-based defenses. By evaluating each device before allowing access to corporate networks, these solutions help maintain robust security.
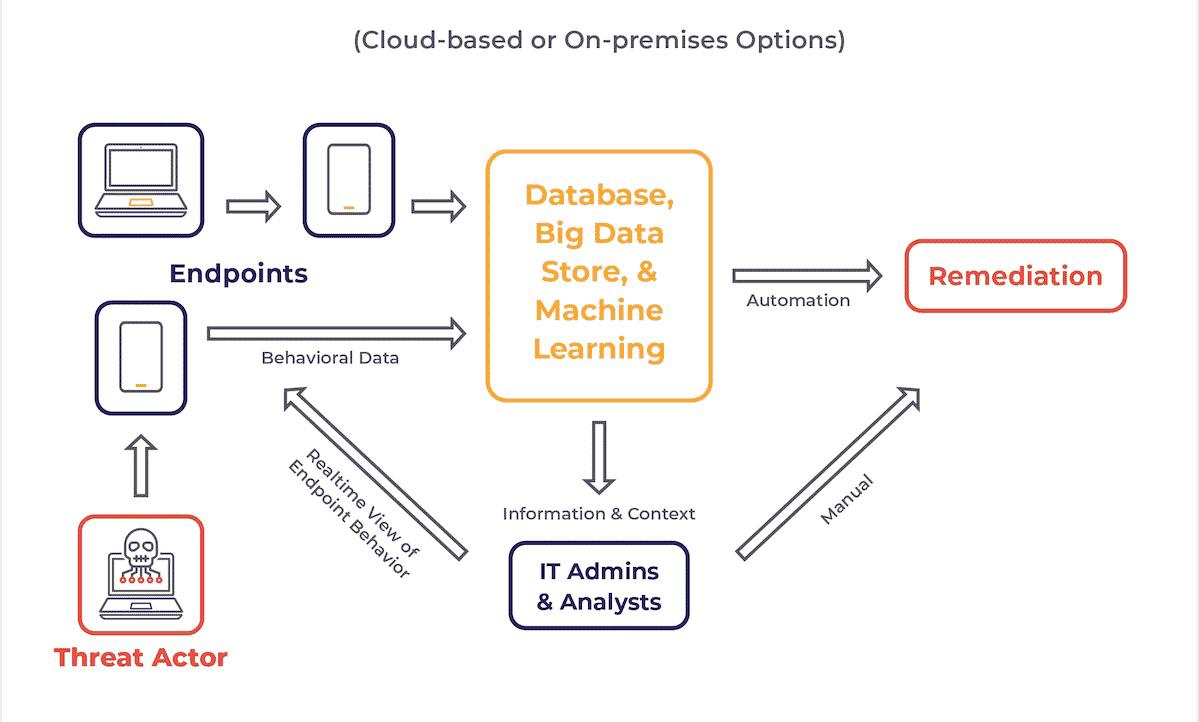
Features and Benefits of Endpoint Security Management Platforms

Policy Enforcement
Ensures that only compliant devices gain access to corporate networks and systems by enforcing security policies across all endpoints.

Improved Threat Management
Identifies and blocks risky devices, provides ongoing monitoring of device security, and enhances threat detection and response for connected endpoints.

Simplified Policy Management
Allows easier definition and management of security policies with a single console, enabling scalability as endpoint numbers increase.

Security Agility
Centralized policy management allows for quick updates to security policies, ensuring rapid responses to evolving security threats and industry best practices.

Endpoint Visibility
Provides deep visibility into every device attempting to access corporate resources, collecting data on each device’s security posture.
In summary, endpoint security management is essential for protecting modern corporate networks from potential security risks posed by various devices, whether managed by the organization or personally owned by employees.
Hackers Never Sleep. Neither Do We.
DUBAI OFFICE
+971-54-565-9528
Digisecuritas Cybersecurity, FZCO 52550-001, IFZA Business Park, Dubai Digital Park, Dubai Silicon Oasis, Dubai, UAE
INDIA OFFICE
+91-8196966161, +91-8194943131
SCO 27, Level-II, Sector 21C, Sector 21, Chandigarh, 160022
