Cybersecurity Gap Analysis
An IT Security GAP Analysis is a systematic approach to evaluating an organization's security posture against established standards or frameworks. This analysis helps identify deficiencies and areas for improvement in security controls, policies, and procedures.
Steps Involved in Conducting a GAP Analysis
- Scope Definition: Clearly outline the boundaries of the analysis, including the systems, processes, and assets involved. Identify relevant security standards or regulations, such as ISO 27001 or the NIST Cybersecurity Framework.
- Data Collection: Gather comprehensive information regarding current security measures. This may involve reviewing documentation, interviewing key personnel, and conducting technical assessments like vulnerability scans.
- Gap Identification: Compare existing security practices against the desired state defined by the selected benchmark. Identify any shortcomings in controls and practices, mapping them to specific requirements.
- Risk Assessment: Evaluate the potential impact and likelihood of identified gaps. Prioritize these gaps based on their risk to organizational assets and compliance obligations.
- Remediation Planning: Develop a strategic plan to address the identified deficiencies. Prioritize remediation activities according to risk assessment findings, specifying actions, timelines, responsible parties, and expected outcomes.
- Implementation and Monitoring: Execute the remediation plan by implementing necessary controls and procedures. Continuously monitor progress to ensure timely and effective changes are made.
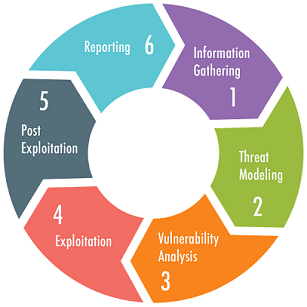
Relationship with IT Security Audits
An IT Security GAP Analysis often complements IT Security Audits. While the GAP Analysis identifies deficiencies, an audit assesses the effectiveness of existing controls against applicable standards and regulations. The audit process includes reviewing documentation, interviewing personnel, and performing technical evaluations.The findings from a GAP Analysis can inform the audit process by highlighting areas needing attention. Together, these evaluations provide organizations with critical insights into their security posture, supporting risk mitigation efforts and compliance enhancement.By conducting both a GAP Analysis and an audit, organizations can develop a robust IT security program that effectively addresses vulnerabilities and strengthens overall security measures.
Hackers Never Sleep. Neither Do We.
DUBAI OFFICE
+971-54-565-9528
Digisecuritas Cybersecurity, FZCO 52550-001, IFZA Business Park, Dubai Digital Park, Dubai Silicon Oasis, Dubai, UAE
INDIA OFFICE
+91-8196966161, +91-8194943131
SCO 27, Level-II, Sector 21C, Sector 21, Chandigarh, 160022
